If you’re in the IT or Security world, you’ve undoubtedly been bombarded with “Zero Trust” talk over the last few years. It’s become the pumpkin spice latte but for cybersecurity.
Although Zero Trust has become a bit of an overused buzzword, you might feel like you should have a better handle on what it means by now and what you need to do about it. In this article, we’ll dive into the key components of Zero Trust and provide you with some practical tips to get started with a strategy that fits your security and business goals.
The Basics of Zero Trust
Zero Trust is a security model gaining popularity due to its ability to address modern threats and risks posed by cloud adoption, remote work, and increasing cyber-attacks. Zero Trust is a comprehensive security strategy beyond a mere product or service. Instead, it focuses on principles for designing and implementing robust security measures. At its core, Zero Trust can be understood through the following principles:
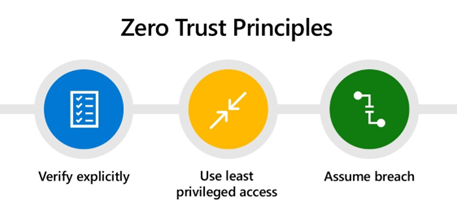
Source: Microsoft’s The critical role of Zero Trust in securing our world
- Verify explicitly: Every access request, regardless of the user or device, must be thoroughly authenticated and authorized before granting entry.
- Use least privilege access: Users are granted only the necessary level of access needed to fulfill their specific roles and responsibilities, minimizing the risk of unauthorized access or misuse of resources.
- Assume breach: Rather than relying solely on network boundaries for security, Zero Trust assumes that attackers may already be present within the network and continuously checks and analyzes activities to detect and mitigate potential threats.
Now that we have explored the basics of Zero Trust and its core principles, let’s delve into applying these principles through different frameworks and the Zero Trust Technology Pillars.
Zero Trust Pillars
There are several frameworks to apply Zero Trust principles. Each source usually puts its own spin on things with slightly different names or grouping for domains. However, they follow the same domains known as Zero Trust Technology Pillars.
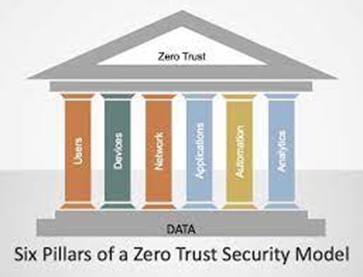
Source: ACT-IAC Zero Trust Cybersecurity Current Trends
While different organizations may define Zero Trust pillars differently, here is a common set of pillars that form the foundation of a Zero Trust architecture.
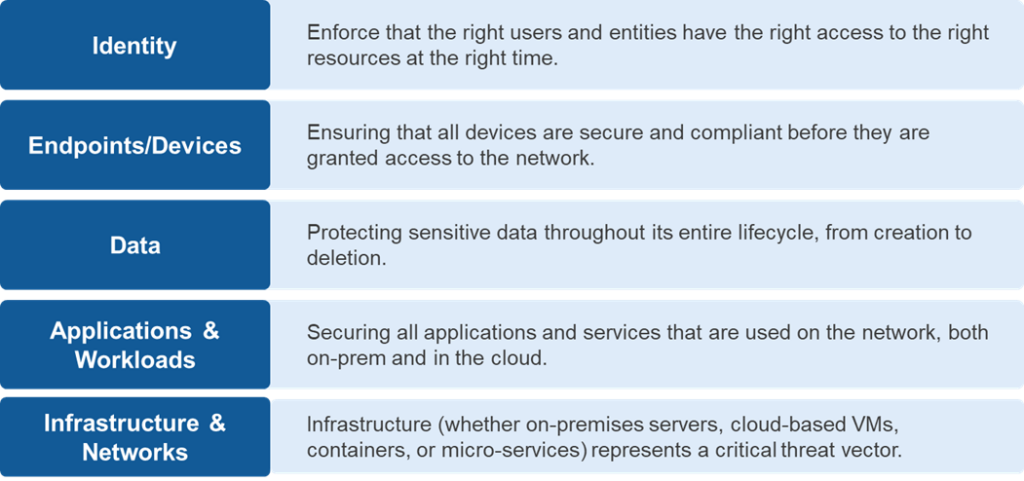
In addition, Zero Trust includes three cross-cutting capabilities that apply across all Technology Pillars.

Now that we have covered the fundamentals of Zero Trust principles and pillars let’s take a moment to understand how it differs from our traditional approach to security.
Traditional vs. Zero Trust Architecture
The picture below shows the difference between the traditional perimeter-based security model and the Zero Trust architecture. The old model relies on a central network boundary, which is no longer effective in today’s complex IT landscape. In contrast, Zero Trust is gaining popularity because it removes the notion of trust from the network structure. It brings security to users, data, applications, APIs, devices, networks, and the cloud, regardless of their location. Instead of confining them to a presumed “secure” network, Zero Trust ensures protection everywhere. This shift in approach transforms security from being seen as restrictive to enabling businesses. (Sources: “Zero Trust Core Principles” – The Open Group and Microsoft’s ‘From security perimeter to Zero Trust’)
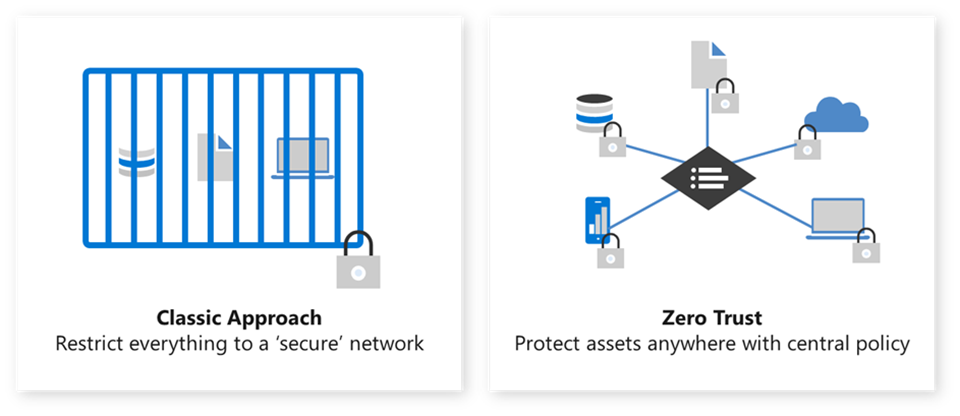
Microsoft’s ‘From security perimeter to Zero Trust’
History of Zero Trust
Zero Trust has evolved, and a few notable milestones have shaped the development that supplies insight into why we’re seeing a ramp-up in Zero Trust buzz over recent years and months.

The events above have produced many well-known Zero Trust Guides, Maturity Models, and resources. In the following list, we’ll share a few of the well-known resources you may want to explore (not an exhaustive list).
Key Zero Trust Resources
- Forrester Zero Trust Model: Revolutionize Your Security With Forrester’s Zero Trust Model and The Definition Of Modern Zero Trust.
- NIST Zero Trust Architecture: The National Institute of Standards and Technology (NIST) Zero Trust Architecture (800-207) focuses on continuous monitoring, assessment, and authorization of all devices, users, and data.
- Cybersecurity & Infrastructure Security Agency (CISA): Zero Trust Maturity Model and Cloud Security Technical Reference Architecture with specific examples of traditional, initial, advanced, and optimal zero trust architectures within each pillar.
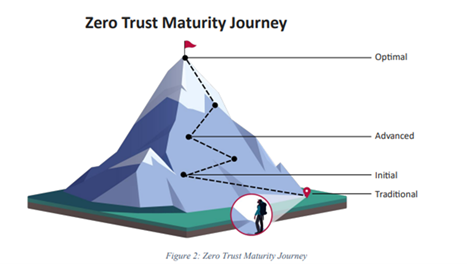
Source: Zero Trust Maturity Model - Cloud Security Alliance (CSA): A Resource Hub called the Zero Trust Advancement Center supplies many events, training, and guidance, keeping you updated on everything Zero Trust across industries.
- DoD Zero Trust Strategy: For those tracking the rise of Zero Trust within the Government space, the release of the DoD Zero Trust Strategy has been a huge marker in the progression of DoD’s progress towards implementing Zero Trust requirements. The strategy defines specific actions that break into a series of associated activities for DoD to work towards across each level. These are commonly referred to as the ‘152 Zero Trust Activities’ within the DoD community.
- Target Activities: 91
- Advanced Activities: 61
- Total Activities: 152
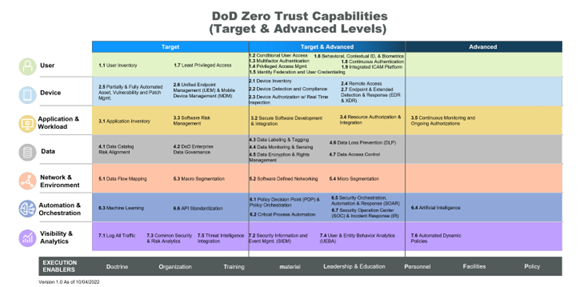
Source: DoD Zero Trust Strategy
Now that we’ve reviewed some valuable resources let’s switch gears and talk about how security tools help with adopting Zero Trust.
Benefits of Using Microsoft Zero Trust Solutions
It’s important to remember that Zero Trust is not a tool or technology but a security framework. However, some solutions supply ways to implement and automate Zero Trust Security principles and accelerate your path.
Microsoft has gone all in on aligning its services with Zero Trust, including many native security capabilities designed around each pillar of Zero Trust. The following diagram visualizes some key Microsoft solutions that align with the Zero Trust technology pillars.
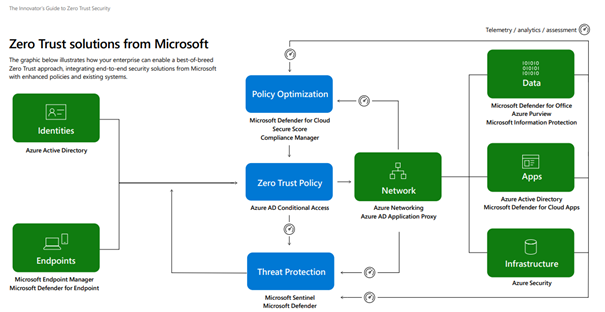
Source: Microsoft’s Evolving Zero Trust Whitepaper
Through our experience deploying these security solutions, we have captured many lessons learned, including the following benefits:
- Integration: The solutions combine tools and services, making implementing Zero Trust across your infrastructure easier without dealing with disparate solutions.
- Deep ecosystem integration: The solutions work well with the existing Microsoft ecosystem, allowing customers to use current investments and maximize their value.
- Vital security intelligence: Microsoft has a wealth of global network and threat intelligence resources, enabling customers to stay ahead of emerging threats and implement proactive security measures.
- Scalability and flexibility: The solutions are scalable and adaptable, accommodating our organization’s growth and changing needs.
- Centralized management: Supplies user-friendly interfaces and centralized management consoles, simplifying the configuration, monitoring, and management of our Zero Trust policies.
- Compliance and industry standards: The solutions align with best practices and follow regulatory standards, ensuring we effectively meet our security and compliance requirements across various requirements.
Helpful resources to dive deeper:
- AIS and Microsoft Hosted Webinar: Demystifying Zero Trust
- Zero Trust Guidance Center
- Evaluate your Zero Trust security posture (assessment survey)
- Attack Use Cases and Solutions
- Zero Trust illustrations for IT architects and implementers
- Microsoft Cybersecurity Reference Architectures
- Microsoft Zero Trust Security Blog Site
Now that we have covered the requirements and explored relevant resources let’s shift gears and look at practical ways to apply all these elements as part of a comprehensive journey toward implementing a Zero Trust strategy.
A Practical Zero Trust Strategy
So you want to implement a Zero Trust strategy? Draw from the AIS’ Security Delivery Framework (SDF), which combines steps from various frameworks, including Zero Trust and Risk Management Framework (RMF), to create a comprehensive model for continuous security enhancement.
To begin your Zero Trust journey, it is crucial to align your security strategy with regulatory requirements while incorporating Zero Trust principles. Our approach focuses on compliance and ongoing security improvements tailored to your organization’s goals.
THE AIS SECURITY DELIVERY FRAMEWORK
By following these steps, you can confidently secure your cloud.
Summary
Zero Trust is a security model gaining traction among organizations of all sizes to enhance their security posture and protect against advanced threats. Organizations can protect their data and infrastructure from cyber threats by implementing a Zero Trust security model and AIS practical steps.
How AIS Can Help
If you want to explore our Security capabilities or determine your eligibility for a complimentary “Zero Trust Security Assessment” of your Microsoft Cloud Environment, contact AIS today. We are here to provide further information and support your security initiatives.






