Point-to-Site Virtual Private Network (VPN) connections are helpful when you want to connect to your VNet from a remote location. This helps us securely connect individual clients running Windows, Linux, or macOS to an Azure VNet. This blog will outline steps to create and test a Point to Site VPN while using an Azure Certificate Authentication method.
Create a VNet
Sign in to the Azure portal.
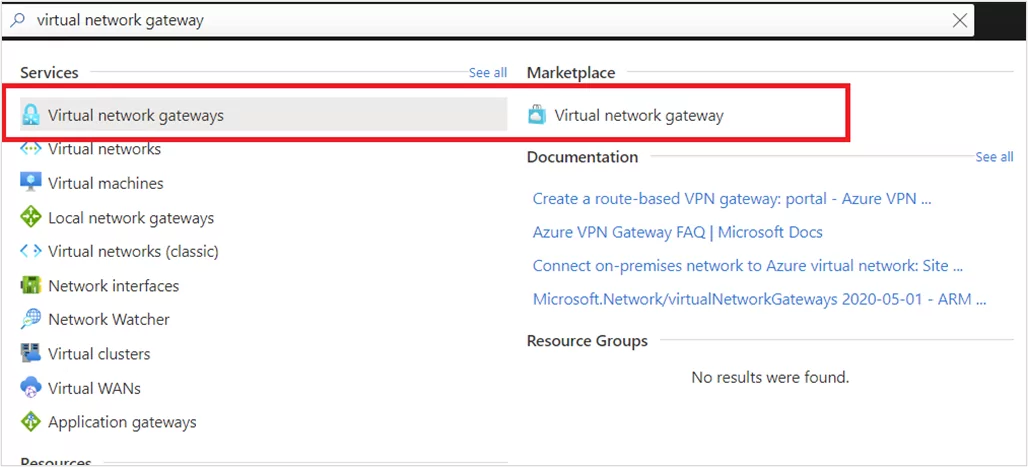
In Search, type Virtual Network.
Select Virtual Network from the Marketplace results.
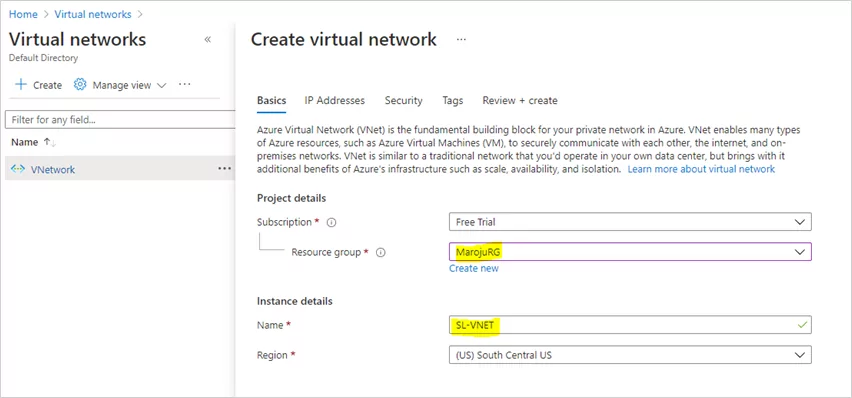
Once you select Create, the Create virtual network page will open.
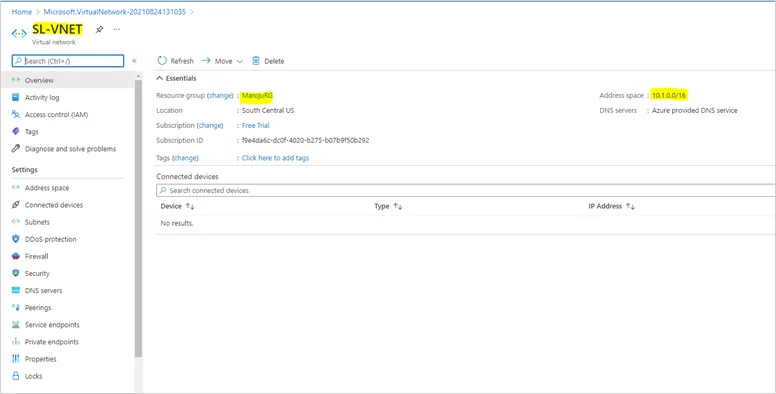
On the Basics tab, configure Project details and Instance details VNet settings.
Create the VPN Gateway
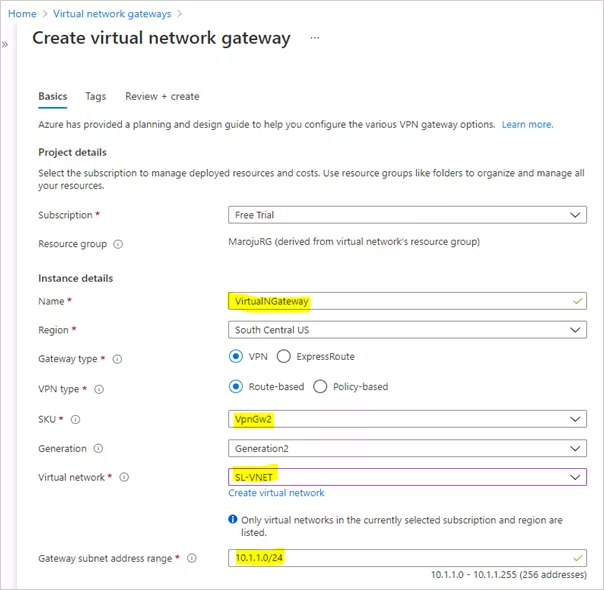
A VPN gateway is a specific type of virtual network gateway used to send encrypted traffic between an Azure virtual network and an on-premises location over the public Internet. Each virtual network can have only one VPN gateway. The virtual network gateway uses a specific subnet called the gateway subnet. The gateway subnet is part of the virtual network IP address range you specify when configuring your virtual network. It contains the IP addresses that the virtual network gateway resources and services use.
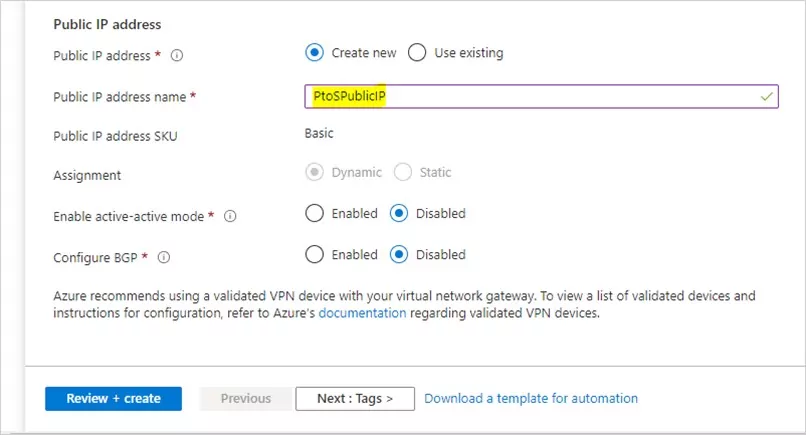
On the Basics tab, fill in the values for Project details and Instance details.
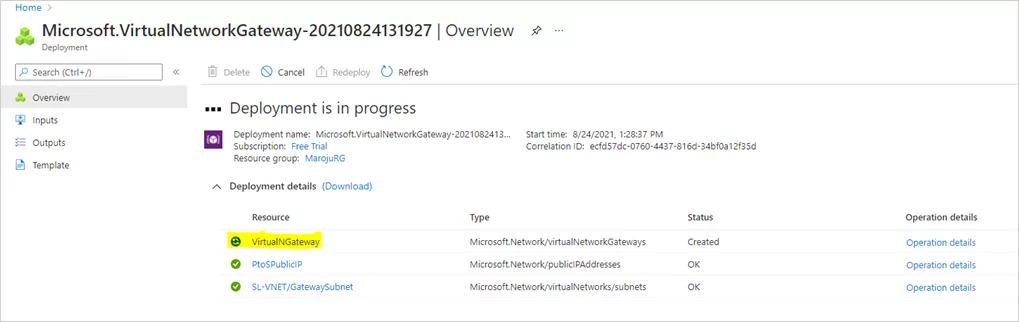
Note: Deployment of the virtual network gateway may take up to 45 minutes.
Looking to grow your career in Azure? We're growing quickly and we're looking for talent to join the team. View our open career opportunities today.
Generating Certificates
Azure uses certificates to authenticate clients connecting to a VNet over a Point-to-Site VPN connection. Once you obtain a root certificate, you upload the public key information to Azure. The root certificate is then considered ‘trusted’ by Azure to connect P2S to the virtual network. You also generate client certificates from the trusted root certificate and then install them on each client computer. The client certificate is used to authenticate the client when it initiates a connection to the VNet.
Generate a Root Certificate
Use either a root certificate generated with an enterprise solution (recommended) or generate a self-signed certificate. After creating the root certificate, export the public certificate data (not the private key) as a Base64 encoded X.509 .cer file. Then, upload the public certificate data to the Azure server.
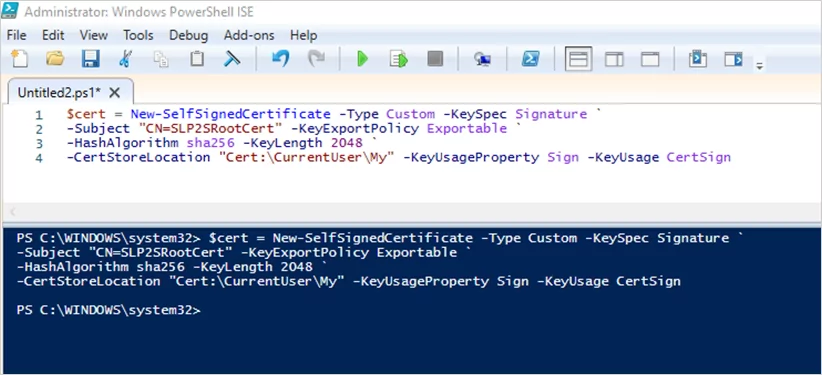
Open PowerShell as an Administrator and run the following script.
$cert = New-SelfSignedCertificate -Type Custom -KeySpec Signature ` -Subject “CN=SLP2SRootCert” -KeyExportPolicy Exportable ` -HashAlgorithm sha256 -KeyLength 2048 ` -CertStoreLocation “Cert:\CurrentUser\My” -KeyUsageProperty Sign -KeyUsage CertSign
This will create a root cert and install it under the current user cert store.
Generating Client Certificates from Root Certificate
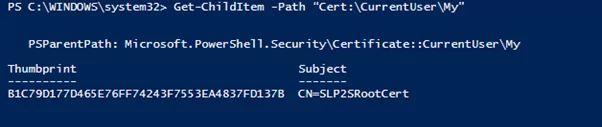
Open PowerShell as an Administrator and run the following command:
Get-ChildItem -Path “Cert:\CurrentUser\My”
This should provide a thumbprint:
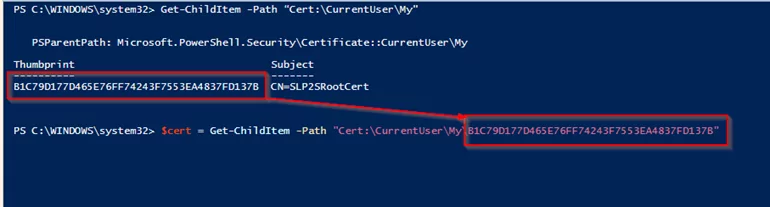
Next, run the following command. The thumbprint should mutch to your Certificate.
$cert = Get-ChildItem -Path “Cert:\CurrentUser\My\B1C79D177D465E76FF74243F7553EA4837FD137B”
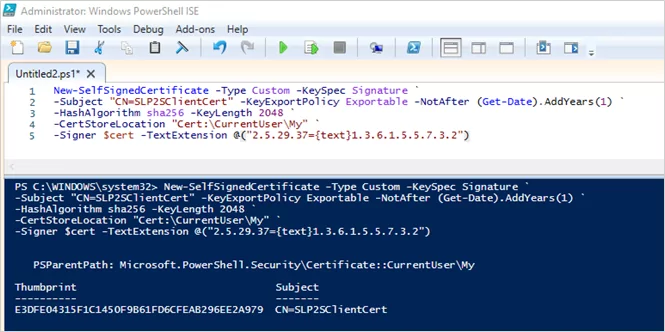
Finally, you’ll need to run this to generate your client certificate.
New-SelfSignedCertificate -Type Custom -KeySpec Signature `
-Subject “CN=SLP2SClientCert” -KeyExportPolicy Exportable -NotAfter (Get-Date).AddYears(1) `
-HashAlgorithm sha256 -KeyLength 2048 `
-CertStoreLocation “Cert:\CurrentUser\My” `
-Signer $cert -TextExtension @(“2.5.29.37={text}1.3.6.1.5.5.7.3.2”)
We now have certs in place, But we need to export the root certificate to upload it in Azure.
First, export the root certificate public key (.cer)
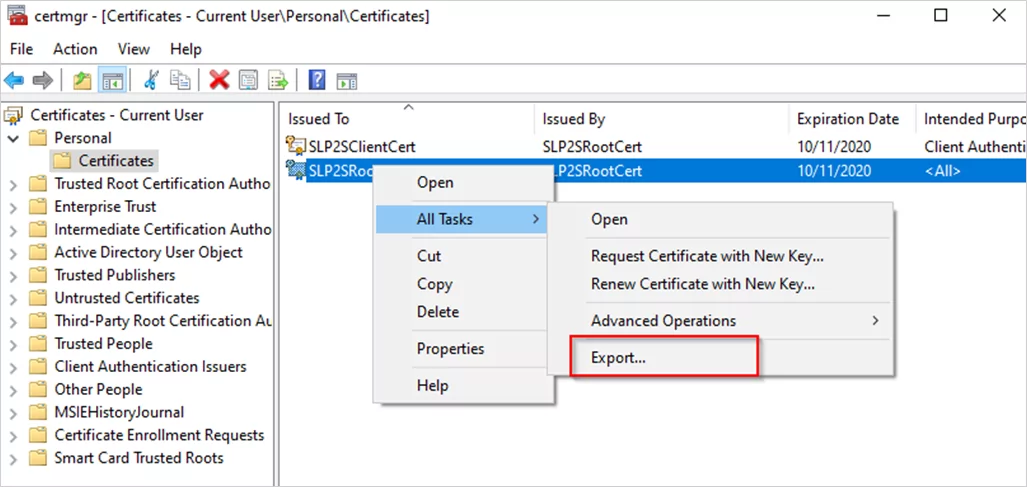
Hit the Windows Key + “R”, to bring up the Run dialog box and type in “certmgr.msc”. When the management console opens, you should see your newly created certificate in “Current User\Personal\Certificates”. Right-click on your newly created cert and go to All Tasks > Export.
In the Wizard, click Next.
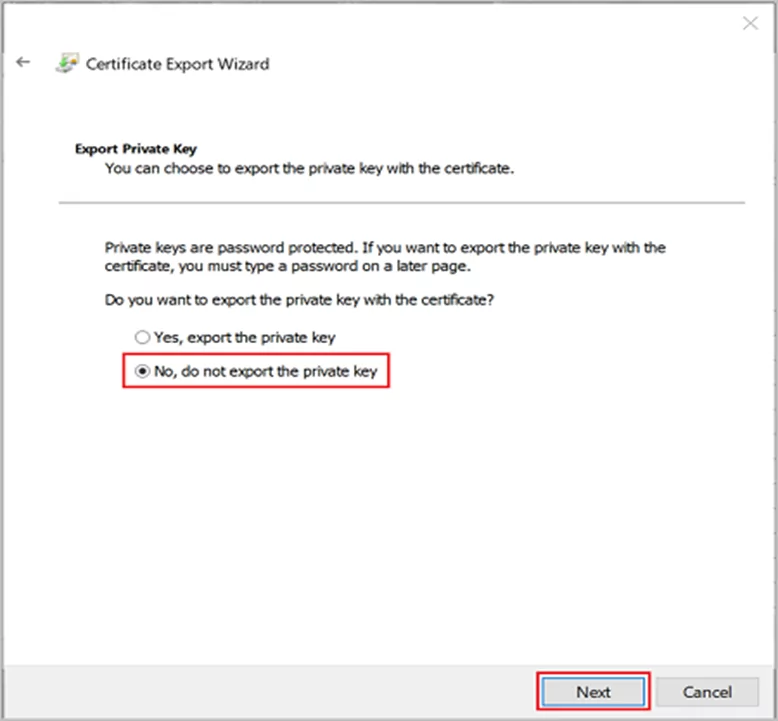
Select No, do not export the private key, and then click Next.
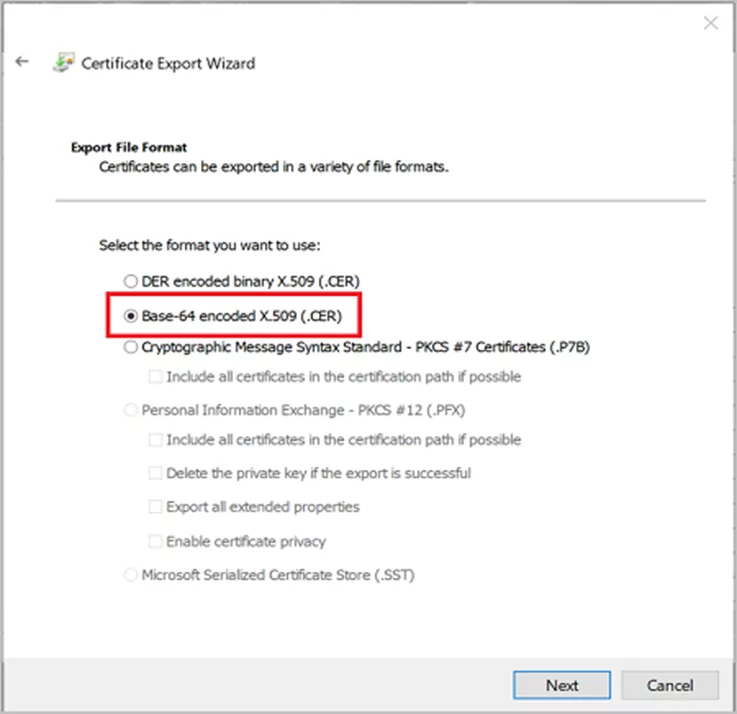
On the Export File Format page, select Base-64 encoded X.509 (.CER)., and then click Next.
For File to Export, Browse to the location to which you want to export the certificate. Specify your file name. Then, click Next.
Click Finish to export the certificate. Your certificate is successfully exported!
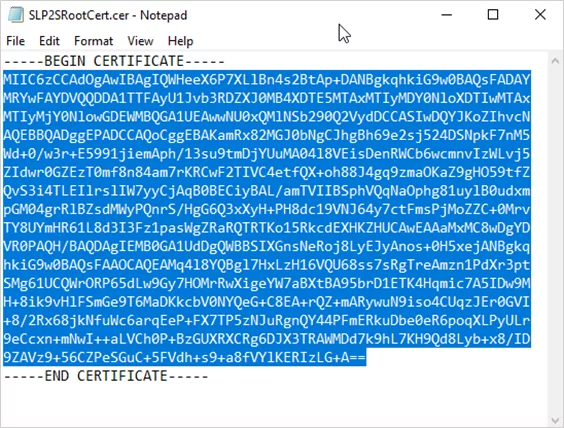
The exported certificate looks similar to this:
If you open the exported certificate using Notepad, you see something similar to this example. The section in blue contains the information that is uploaded to Azure. If you open your certificate with Notepad and it does not look similar to this, typically, this means you did not export it using the Base-64 encoded X.509(.CER) format. Additionally, if you want to use a different text editor, some editors can introduce unintended formatting in the background. This can create problems when uploading the text from this certificate to Azure.
Configure Point to Site Connection
- The next step of this configuration is to configure the point-to-site connection. Here we will define the client IP address pool as well. It is for VPN clients.
- Click on the newly created VPN gateway connection.
- Then in a new window, click on Point-to-site configuration
- Click on Configure Now
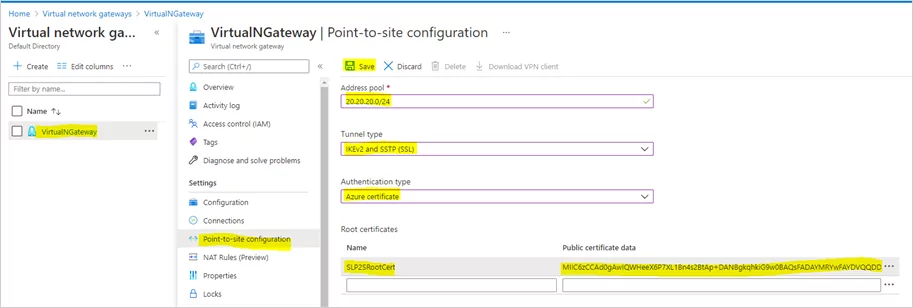
- In a new window, type the IP address range for the VPN address pool. We will be using 20.20.20.0/24. For tunnel, type use both SSTP & IKEv2. Linux and other mobile clients, by default, use IKEv2 to connect. Windows also use IKEv2 first and then try SSTP. For authentication type, use Azure Certificates.
- In the same window, there is a place to define a root certificate. Under root certificate name, type the cert name and under public certificate data, paste the root certificate data ( you can open cert in notepad to get data).
- Then click on Save to complete the process.
- Note: when you paste certificate data, do not copy —–BEGIN CERTIFICATE—– & —–END CERTIFICATE—– text.
Testing VPN Connection
Log in to Azure portal from the machine and go to VPN gateway configuration page.
Click on Point-to-site configuration.
Next, click on Download VPN client.
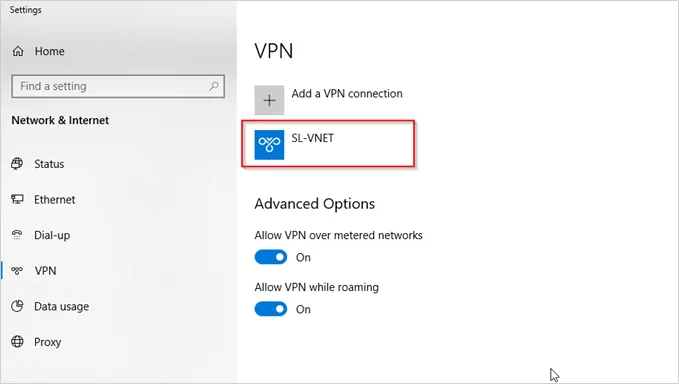
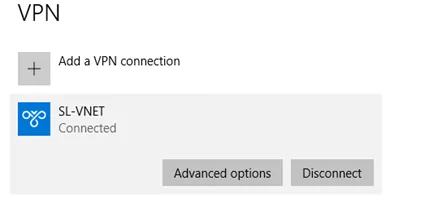
We can see a new connection under the windows 10 VPN page.
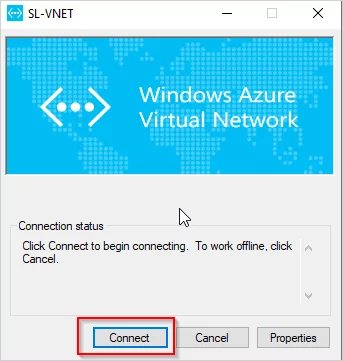
Click on connect to VPN. Then it will open this new window. Click on Connect.
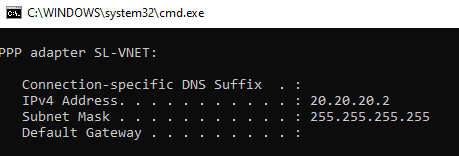
Run ipconfig to verify IP allocation from VPN address pool.
Congratulations! You’ve successfully configured a Point to Site VPN Connection using Azure Certificate Authentication.
AIS has been working with Azure since 2008. Interested in learning more? Reach out to AIS today.