While recently working on moving an FTP server (using Passive FTP) from on-premises to Azure, I needed to expose the FTP server to the internet via an Azure External Load Balancer. A few things were not well documented. I thought it would be good to put together a step-by-step guide on setting up the load balancer, configuring the FTP server on the backend, and setting the Network Security Group rules associated with the FTP server. In this example, the FTP server will be running on IIS, and it is assumed that there is no Azure Firewall\NVA associated with the VNET that is hosting the FTP server. Suppose your environment does have an Azure Firewall\NVA. In that case, there will be an additional Azure resource needed, an Azure Route Table with a 0.0.0.0\0 out to the internet associated with the subnet the FTP server is hosted. This is required in order to route the outbound traffic back out to the internet. If this is not done the outbound FTP traffic will die on the Azure Firewall\NVA.
Windows IIS FTP Server Configuration
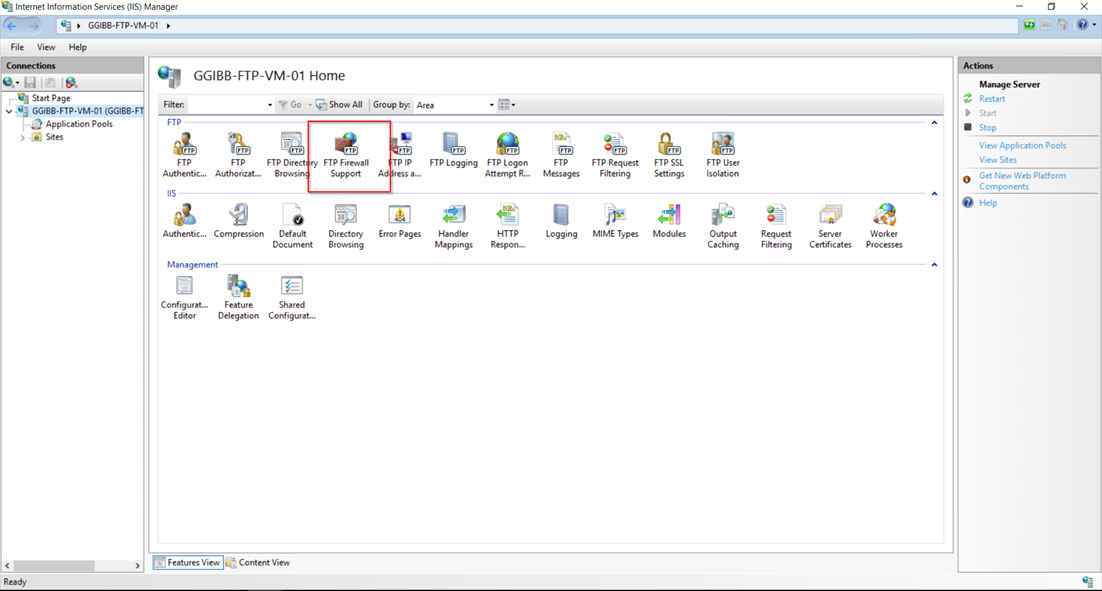
I won’t be going into the details of the FTP server configuration here. I will just be going over the FTP firewall settings and set the Data Channel Port (Passive FTP Ports). Below is how the FTP server is configured to support the external load balancer. On the IIS server settings – FTP Firewall Support is where you define the Data Channel Port Range.
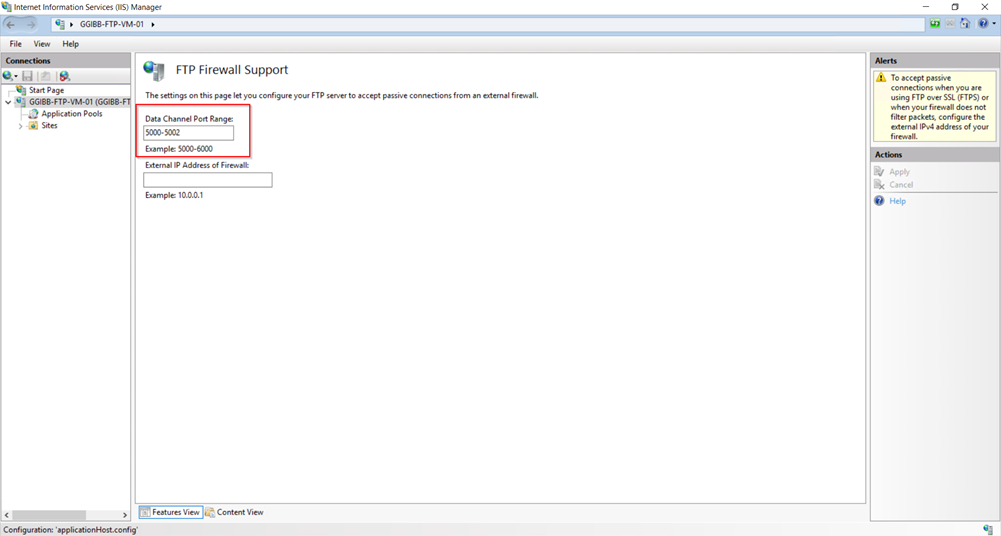
I have defined ports 5000-5002.
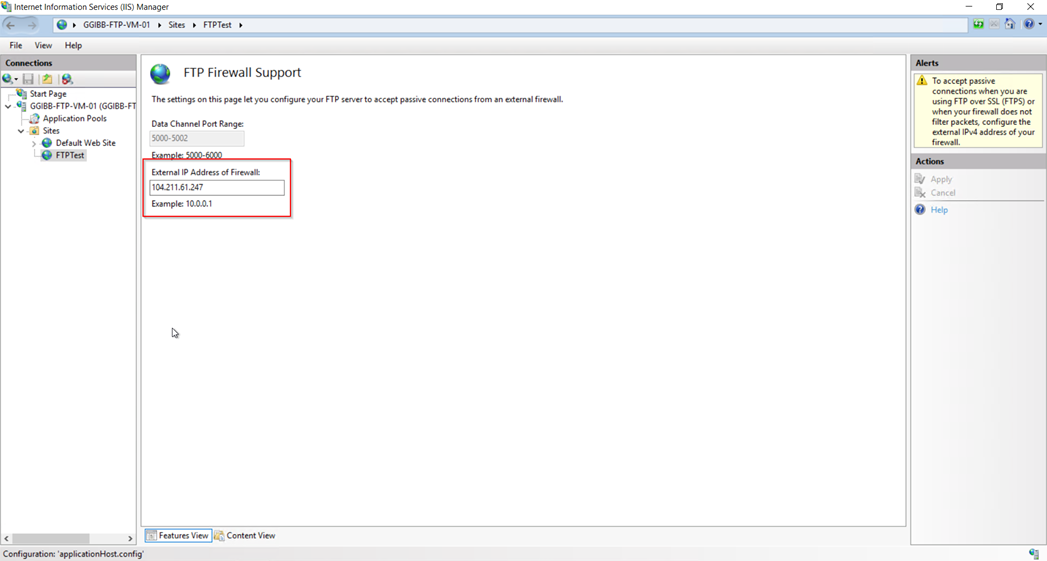
At the site, the level is where you configure the public IP address of the external load balancer.
As you see in the screenshot below the public IP of the external load balancer is configured.
Azure External Load Balancer
Configuring an Azure External Load Balancer for FTP is strait forward. One thing to note with Passive FTP is that all the Data Channel ports for FTP must be defined in the load balancing rules. If you define ports 5000-5100, there will be 100 load balancing rules for each data channel port. I recommend keeping the number of passive ports to a minimum since Azure External Load Balancers do not support a port range.
Requirements:
- Azure Public IP – this will be configured as the load balancer’s front-end IP
- Azure Load Balancer
- FTP Port requirements for inbound traffic and public IP address(es) of the client(s) that will be accessing the FTP server
Deploy the Load Balancer
Search for Azure Load Balancer in the search bar in the Azure Portal
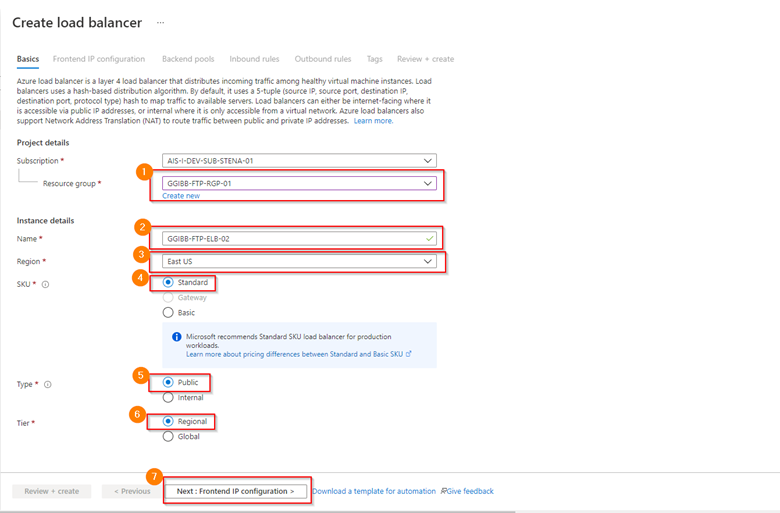
Define the following parameters then select Next: Frontend IP configuration
- Resource Group
- Name
- Region
- Leave SKU: Standard
- Leave Type: Public
- Tier: Region
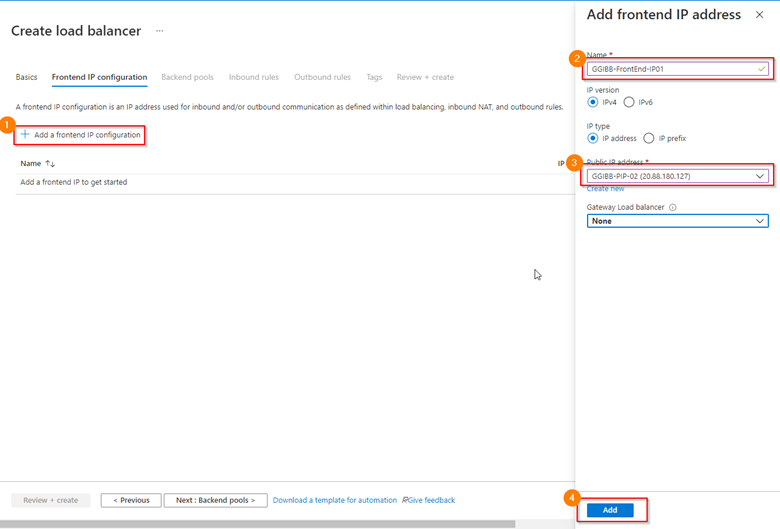
Select Add a frontend IP Configuration, define the following parameters
- Frontend IP Name
- IP version: leave IPv4
- IP type: leave IP address
- Public IP address
- Gateway Load balancer: leave None
Select Add
Select Review + create – we will go over the configuration of the remaining items of the Load Balancer after it has been deployed.
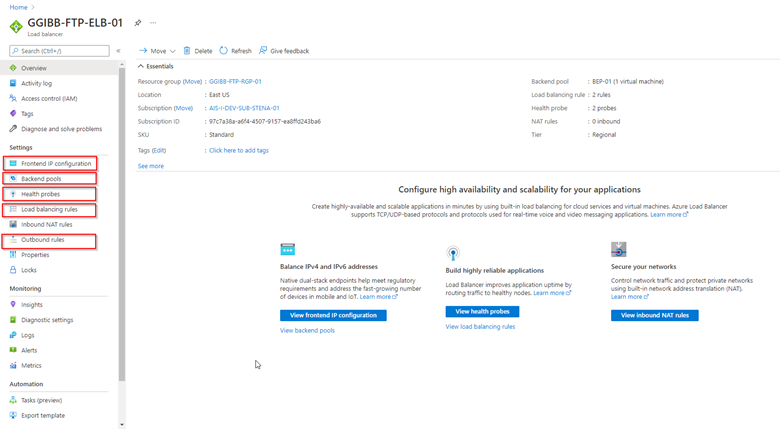
Configuration of the Azure External Load Balancer
I will now go over the configuration of the Azure Load Balancer. This will detail how the Backend pool, Health probes, Load balancing rules, and Outbound rules are configured.
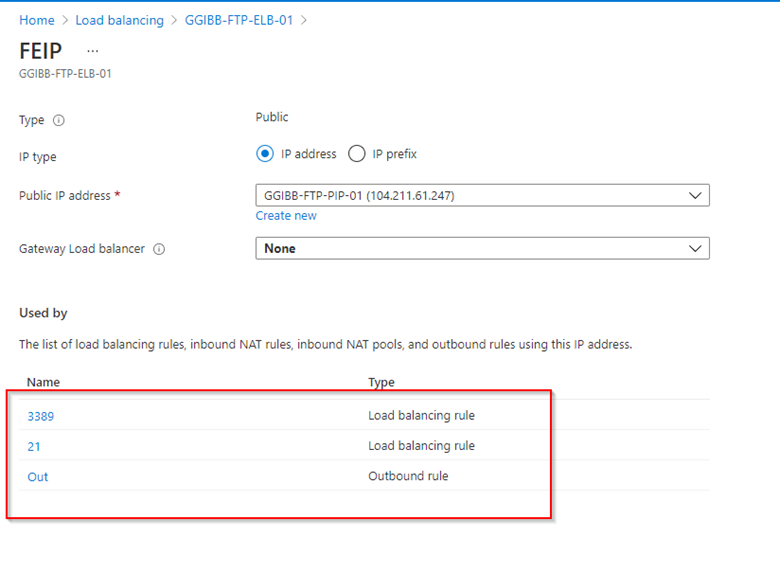
Frontend IP Configuration
As you see in the screenshot below, the frontend IP is defined by the rules associated with the front end. After additional load balancing rules are added I will review the frontend configuration again.
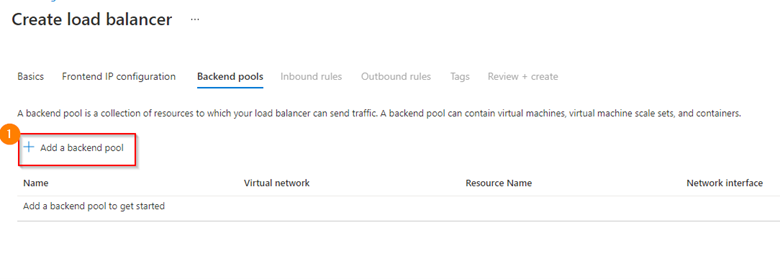
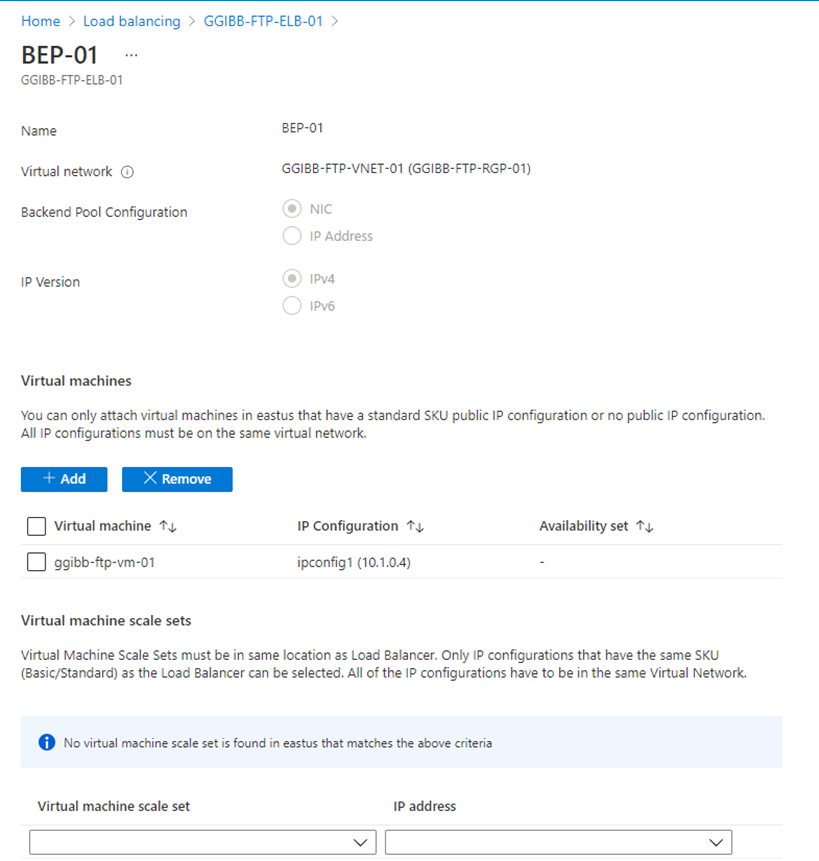
Backend Pools
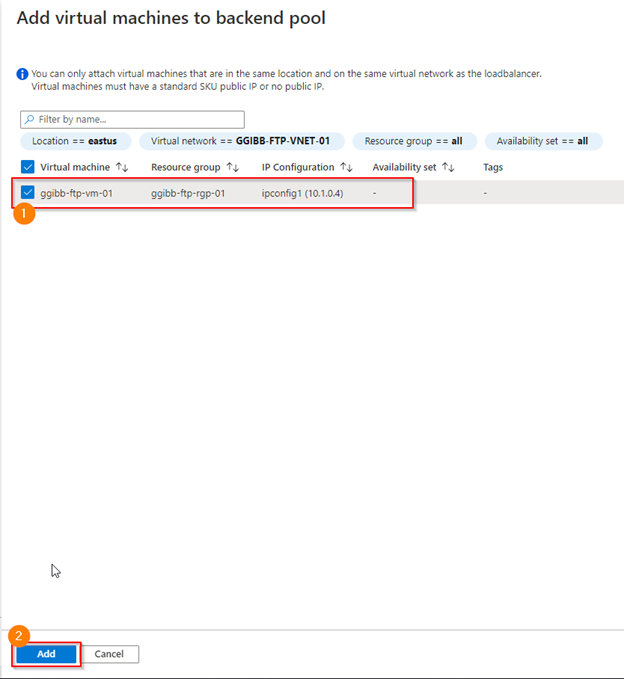
The backend pool configuration is how you associate a virtual machine with the load balancer. In the screenshot below, I use the following configuration
- Virtual network – the VNET that the target virtual machine is associated with
- Backend Pool Configuration: NIC
- IP Version: IPv4
- Add the virtual machine by selecting the +Add button
- Select Save
Health Probes
I have created an FTP Health probe for port 21. I will also be using this health probe for my FTP data channel ports. You can make a health probe for each data channel port.
- Name: FTP
- Protocol: TCP
- Port: 21
- Interval: 5
- Unhealthy threshold:2
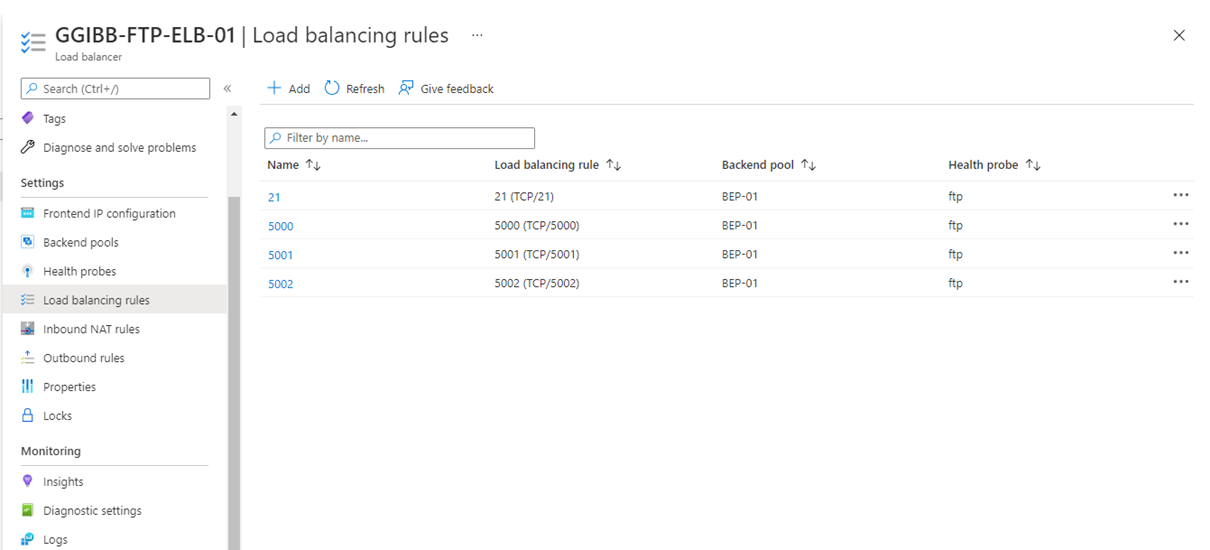
Load Balancing Rules
I have the port 21 load balancing rule already configured but need to add the FTP data channel ports that I have defined in FTP Firewall (5000-5002).
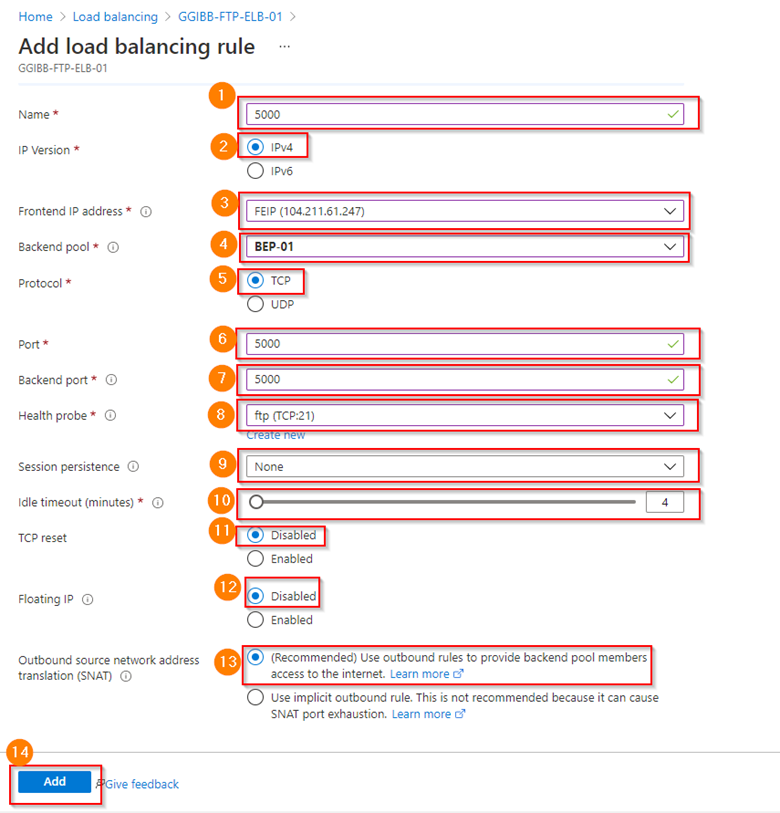
Define the following parameters:
- Name: I like to give it the name of the port number, in this example, I will use 5000
- IP Version: IPv4
- Frontend IP address: Select your Frontend IP Config – FEIP
- Backend Pool: Select your backend pool – BEP-01
- Protocol: TCP
- Port: 5000
- Backend Port: 5000
- Health Probe: ftp (TCP:21)
- Session persistence: None
- Idle timeout (minutes): 4
- TCP reset: Disabled
- Floating IP: Disabled
- Outbound source network address translation (SNAT): (Recommended) Use outbound rules to provide backend pool members access to the internet
- Select Add
Here is the full set of Load Balancing rules:
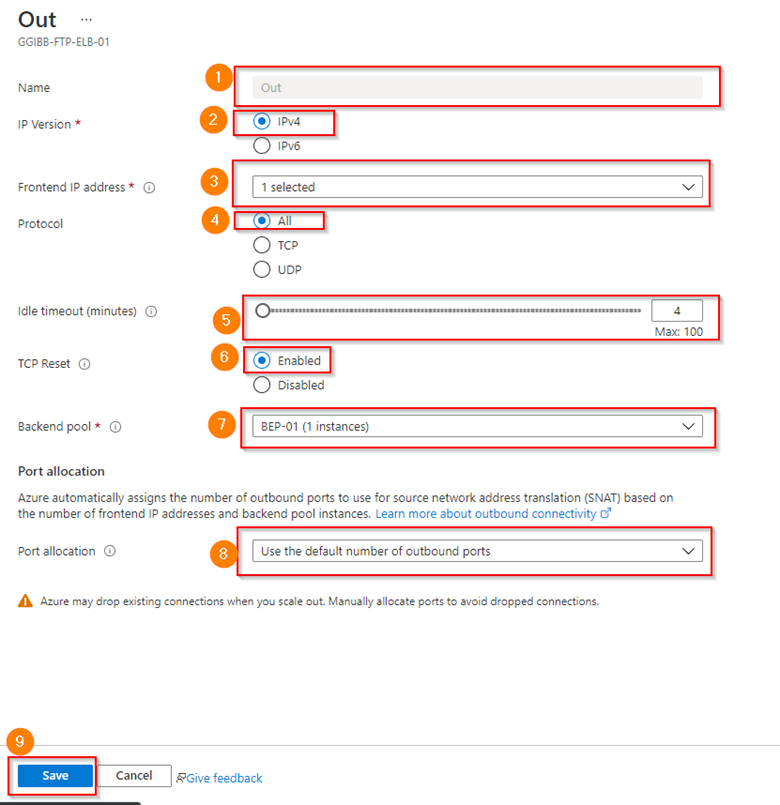
Outbound Rules
There is a requirement to create an outbound rule for the back-end resource to be able to reach out to the internet.
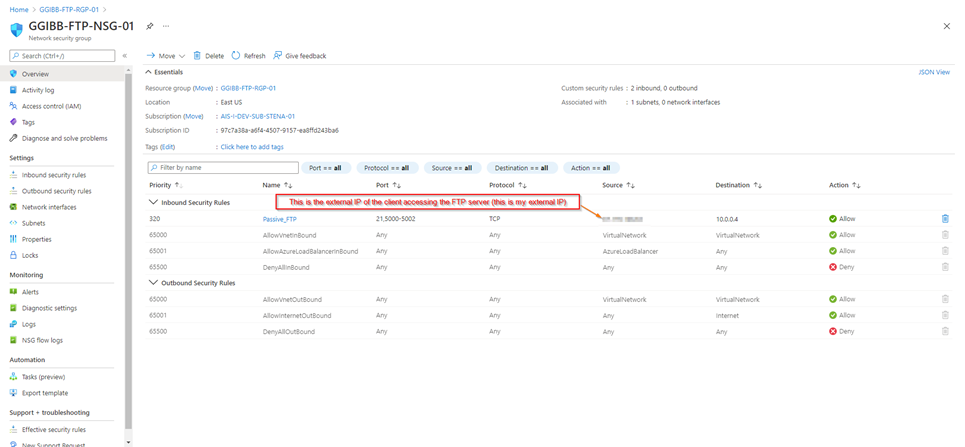
Network Security Group Rules
The final step in configuring this solution is configuring the inbound rules for the NSG. The rule should have TCP ports 21 and the data channel ports defined in your FTP firewall (in my case, this would be 5000-5002).
Conclusion
Passive FTP via an Azure Load Balancer combined with Network Security Group is a great solution to expose your FTP server on the internet securely. Understanding the total possible number of connections at a single time will help determine the minimum number of passive data channel ports required to configure on the Azure External Load Balancer.