DevOps implements a Continuous Integration/Continuous Delivery (CI/CD) process. When multiple team members work in the same codebase, anyone’s update could break the integrated code. So, Continuous Integration is to trigger a build pipeline whenever a code update is pushed. The build pipeline will fail if the newly updated code is incompatible with the existing codebase if there are any conflicts. The codebase might work well within a single developer environment, but in a build pipeline where all configurations and dependencies are expected to be in place can fail. Continuous Delivery speeds up the deployment process. The release pipeline helps to deploy the same code base to multiple environments based on configurations. This helps to support code to be deployed in all environments without many manual changes.
Having an approval process helps peer code reviews, identifies potential issues, and any security flaws ahead of time. The current production applications are very distributed and complex. Whether it is an on-premise or cloud-based solution, missing a dependency or proper configurations could cost significant risk in deployments. DevOps helps to maintain the same code base for repeatable deployment in many environments with just configuration changes. DevOps avoids manually building the deployment packages and handing over to the operations team who would not have insights on what is being deployed. If an error occurs during deployment or post-deployment, then the development team jumps in at that time, which is time-consuming. This will cost in production timeline and end up with some unhappy customers also!
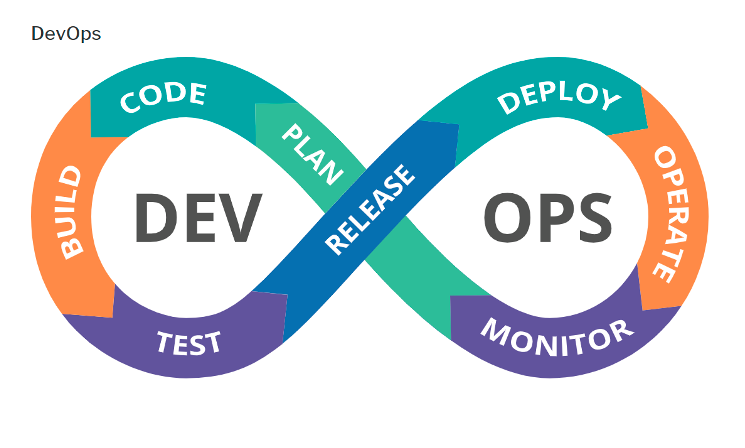 Picture credit: DoD DevOps
Picture credit: DoD DevOps
Popular DevOps Tools
- Azure DevOps – DevOps Pipelines
- GitHub – Git Hub Actions
- GitLab – GitLab Runners
- Jenkins
- CircleCI
- Bamboo
- TeamCity
- Travis
- Buddy
Follow here to learn more about DevOps practices from other AIS bloggers!
Why not just “DevOps”?
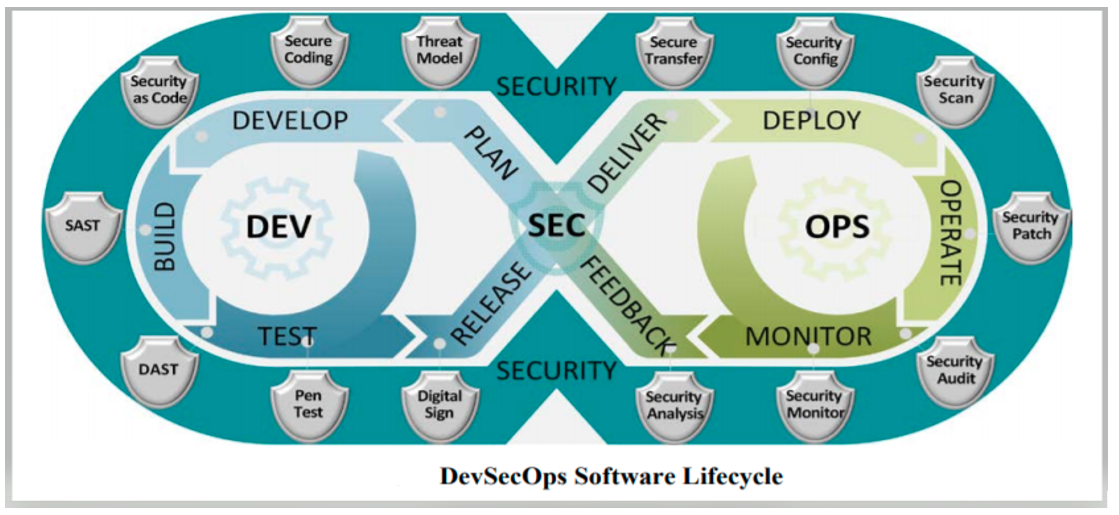
DevOps is fundamental for any organization’s build and deployment process with seamless CI/CD integration. Then, what is ‘DevSecOps’ and why is ‘Sec’ added between Dev and Ops. The ‘Sec’ in DevSecOps is ‘Security.‘ Though it’s added in between, security implementation should start from Development and continue in Operations. As development and deployment packages add many dependencies from both internal and external, this could introduce vulnerabilities. It could cost severe issues in production if not identified earlier in the build pipeline. Code scans help identify possible weaknesses in code implementations. But for any cybersecurity-related vulnerabilities, only specific tools at different stages of the pipeline must be used to identify as early as possible. Adding security scanning earlier in the pipeline and automating are essential for DevSecOps.
Picture Credit: DoD DevSecOps
DevSecOps is not a tool or pattern but a practice and can be enhanced by adding appropriate tools. It is a process in securing the build and deployment by using several security tools by shifting security to the left. These security tools help to identify vulnerabilities that the code could have introduced, recommend possible solutions to fix those issues, and in some instances, the tools can mitigate some of those issues as well. This is to use the ‘fail fast’ method to identify vulnerabilities earlier in the build pipeline. As more applications moved into the cloud, it is highly imperative to follow Cloud Native Computing Foundation (CNCF) certified tools and implement security benchmarks that provided CIS benchmarks. DevSecOps avoids manual changes once the code is in the pipeline, deployed, and deployed. The codebase will be a single source of truth and should not be manipulated at any point.
Adding scanning tools for security and vulnerabilities helps to mitigate any flaws introduced in code and operations. Many open-source tools provide these functionalities. Enabling logging, continuous monitoring, alerting processes, and any self-fix for faster remediation are key for ongoing business operations. Containerizing with hardened container images from DoD Iron Bank helps to protect application container images. Hardened images can be kept up to date from reliable providers. Containers provide cloud-agnostic and no vendor lock-in solutions.
All the security tools in the DevSecOps pipeline must be deployed and running for pipeline scanning in the customer environment. A request will be sent to those security tools from the pipeline code via API request or trigger command-line interface (CLI) commands. Those tools then respond with their findings, statistics, and provide pass/fail criteria. If a tool identifies any vulnerability findings in the scan, then the pipeline will fail.
Deploying the security tools as SaaS services will require permission from the security team. Not all are approved to run in highly secured cloud environments. Those tools all need to be Authority to Operate (ATO) to deploy and configure. Whereas getting the hardened container images for those tools is a safer and secure approach to deploy those tools in the cloud. As the containers are already hardened, which means scanned, secured, and ready to go with all dependencies, they will provide continuous ATO. The hardened container images can be downloaded from DoD Iron Bank, and almost all tool providers provide container images. Many of these providers have different downloads, whether as a software download or a container image. When downloading as a software image, additional tasks to be done to ensure all the dependencies are appropriately configured or should pre-exist. Simultaneously, downloading as hardened container images comes with dependencies and are pre-scanned. The tools can be deployed into Kubernetes in your cloud environment to provide scalable functionality.
Below is a sample DevSecOps pipeline implementation with recommended security tools, as depicted in the picture below:
- Source code pull request is approved by reviewers
- The build pipeline kicks off and code scan is run after a successful initial build
- If any code vulnerabilities are identified, then the pipeline fails
- Build pipeline continues with DAST and PEN testing
- If any vulnerabilities are identified, then the pipeline fails
- Build artifacts are added to private repository either as packages or container
- Repository scan is performed using repository scanning tools and vulnerabilities are reported
- Release pipeline picks up artifacts from private repositories and deploys to Azure (or cloud of your choice)
- Kubernetes is a highly recommended deployment for orchestration, but deployment can be an application of your choice such as Function App, App Service, Azure Container Instances, etc.
- Security has been applied throughout the pipeline process and will continue once the application is deployed. Both native security tools such as Azure Monitor, Azure Security Center, Azure Policies, etc., and third-party tools such as Twistlock, Qualys, etc. Can be used to monitor the health of your production environment.
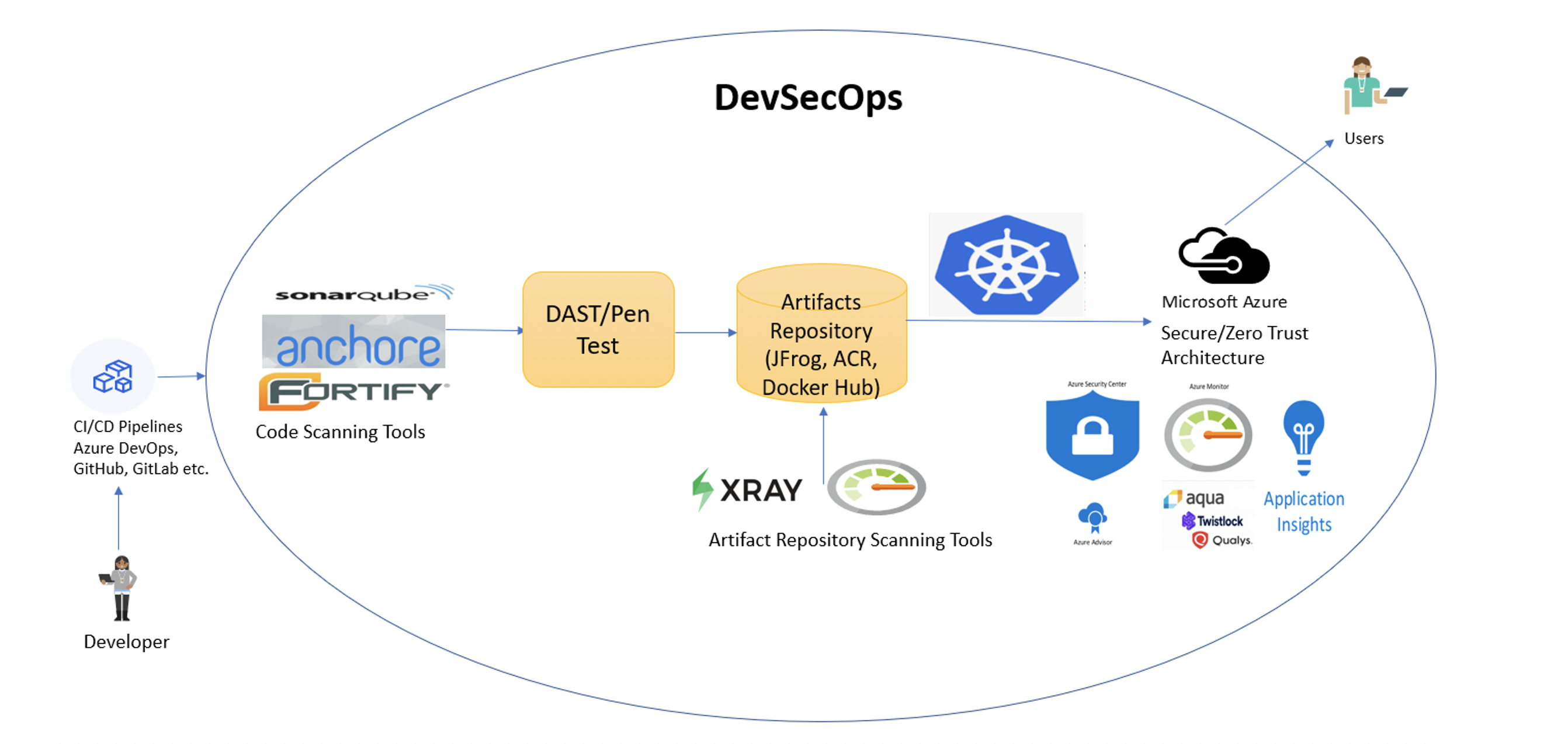
Let’s look at a few of the recommended tools to support the security validations in the DevSecOps process.
Build tools/CLI
A developer can write their code in their favorite editor such as Visual Studio, VS Code, and run/execute to test their applications. The code editor also generates debug/release packages generating binaries using the build tool that comes with the editor. The application works seamlessly from the developer environment as the dependencies and correct configurations exist. For the build to work in the pipeline, the build tool must be available to build the code. Based on the code language, the build tool varies, and they must be available in the pipeline.
Some of the build tools are:
- DotNet Build
- MSBuild
- Maven
- Gradle
Static Application Security Testing (SAST)
A code scan is one of the essential steps in securing the codebase. Automated testing helps identify failures, but these specific code scan tools help identify security flaws and vulnerabilities. The application does not need to be running for code scan tools as it scans only the codebase and not any dependencies.
Some of the Code scanning tools are:
- SonarQube
- Fortify
- Anchore
- JFrog Xray
- OpenSCAP
- HBSS
- OWASP dependency check
Dynamic Application Security Testing (DAST)
DAST scans the application while its running or a container image that is hosted in private repositories. Container scanning before deploying helps resolve many security vulnerabilities.
Some of the DAST scanning tools are:
- Twistlock Container scans
- Vulnerability Scanning Tools
Penetration (Pen) Testing
Provides Web Applications scanner to help to find security vulnerabilities. Read here to learn about, “Top 10 Web Application Security Risks”
PEN testing tools:
- OWASP ZAP
Deploy Code & IaC (Infrastructure as Code)
IaC is paramount in DevOps to avoid any manual work in customer environments and help with immutable infrastructure.
Popular IaC tools are:
- Azure ARM Templates
- Terraform
- HELM
- Private Repositories
In DevSecOps, a private repository is recommended to host the build dependencies, reference container images, container images for tools, and the built packages or application container images. This is to keep all the artifacts together in one centralized location, and the release pipeline can continue with deployments from there.
Some of the private repositories are:
JFrog
Docker Hub
Azure Container Registry (ACR)
Private Repository Scanning
As the pipeline requires security scanning, the repositories require scanning also. These tools scan for vulnerabilities in all packages and container artifacts stored in the repository. A scan report is being sent/notified for any issues.
Some artifact scanning tools are:
- XRay
- SonaType
- Azure Monitor
- Azure Security Center
Deploy
As the recommendation to deploy the security tools with container orchestration, the same recommendation goes to deployed applications. Containers provide high security with limited ways to be affected by attackers. Sidecar containers protect by continually monitoring applications with a container security stack built-in. Applications are scalable on a demand basis using Kubernetes and tools such as Kubectl; HELM packages are used to deploy and manage K8S clusters. ArgoCD is a declarative tool specifically for Kubernetes deployment in CI/CD pipeline.
Deployments to Azure could be:
- Azure function app
- Azure App Service
- Azure Container Instance
- Azure Kubernetes Service (AKS)
- Open Shift in Azure
- Monitoring/Alerting
Monitoring/Alerting
As the applications deployed and running in a cloud environment, it must be continuously monitored for attacks and identify any security vulnerabilities. For containers, these tools act as sidecar containers to regularly protect main containers from attacks, and some mitigate the issue. All these tools have built-in alert/notify operations team for immediate actions.
Monitoring/alerting tools:
- Azure Monitor
- Azure Security Center
- Twistlock
- Qualys
- Aqua Security
So, all powered up with learning DevSecOps! Follow up back here for the next blog post in container-based deployments and containers scanning in the DevSecOps pipeline!
References for continuing your DevSecOps Journey
- 7 Best CI/CD Tools
- DevSecOps in Azure
- DevSecOps in GitHub
- Red Hat – DevSecOps
- DoD DevSecOps Documents
- DoD DevSecOps Learning Videos
- Security Engineering – Microsoft
- A Beginner-Friendly Introduction to Containers, VMs and Docker
- KodeKloud – for great learning fundamentals for DevOps, Containers, and Kubernetes